1. Why are Network Control Protocols used in PPP?
• to establish and terminate data links
• to provide authentication capabilities to PPP
• to manage network congestion and to allow quality testing of the link
• to allow multiple Layer 3 protocols to operate over the same physical link
2. What is the data transmission rate for the DS0 standard?
• 44 kb/s
• 64 kb/s
• 1.544 Mb/s
• 44.736 Mb/s
3. In which two layers of the OSI model are key differences found between a LAN and a WAN. (Choose two.)
• Layer 1
• Layer 2
• Layer 3
• Layer 4
• Layer 6
• Layer 7
4. Which statement is true about the Cisco implementation of the HDLC protocol?
• It supports authentication.
• It has a universally compatible frame format.
• It is the default encapsulation for serial interfaces on Cisco routers.
• It does not support multiple protocols across a single link.
5. 
Refer to the exhibit. A network administrator has a connectivity problem between the serial interfaces of Merida and Vargas. What is the cause of the problem?
• Authentication is required on the serial link.
• The encapsulation is misconfigured.
• The IP addresses are on different subnets.
• The serial interface on Vargas is shutdown.
• The loopback interfaces on both routers are not configured.
6. 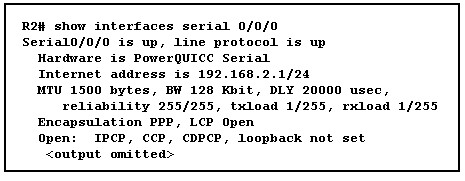
Refer to the exhibit. What statement is true about the exhibited output?
• LCP is in the process of negotiating a link.
• LCP and NCP are waiting for CHAP authentication to complete.
• LCP negotiation has completed successfully, but NCP negotiation is in progress.
• LCP and NCP negotiation is complete, and the data link service is available to carry packets.
7. Which three statements are true regarding LCP? (Choose three.)
• It is responsible for negotiating link establishment.
• It negotiates options for Layer 3 protocols running over PPP.
• It uses MD5 encryption while negotiating link-establishment parameters.
• It terminates the link upon user request or the expiration of an inactivity timer.
• It can test the link to determine if link quality is sufficient to bring up the link.
• It monitors the link for congestion and dynamically adjusts the acceptable window size.
8. Why are Frame Relay paths referred to as virtual?
• Frame Relay PVCs are created and discarded on demand.
• The connections between PVC endpoints act like dialup circuits.
• There are no dedicated circuits to and from the Frame Relay carrier.
• The physical circuits inside the Frame Relay cloud do not contain exclusive links for a specific Frame Relay connection.
9. What best describes the use of a data-link connection identifier (DLCI)?
• an address identifying a virtual circuit
• a logical address identifying the DCE device
• an address identifying a Layer 3 service across a Frame Relay network
• a logical address identifying the physical interface between a router and a Frame Relay switch
10. What two services allow the router to dynamically map data link layer addresses to network layer addresses Frame Relay network? (Choose two.)
• ARP
• ICMP
• Proxy ARP
• Inverse ARP
• LMI status messages
11. Which three statements describe functions of the Point-to-Point Protocol with regards to the OSI model?(Choose three.)
• operates at all layers of the OSI model
• provides a mechanism to multiplex several network layer protocols
• can be configured on both synchronous and asynchronous serial interfaces
• uses Layer 3 of the OSI model to establish and maintain a session between devices
• uses the data link layer to configure such options as error detection and compression
• uses network control protocols to test and maintain connectivity between devices
12. At what physical location does the responsibility for a WAN connection change from the user to the service provider?
• demilitarized zone (DMZ)
• demarcation point
• local loop
• cloud
13. What does a Frame Relay switch use to inform the sender that there is congestion?
• FECN
• BECN
• DE
• FCS
14. 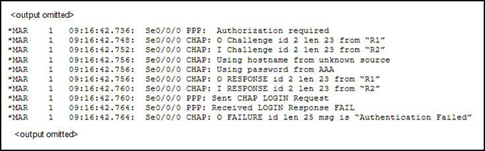
Refer to the exhibit. What statement is true about the debug output?
• R2 is using PAP instead of CHAP.
• The routers have different CHAP passwords configured.
• The administrator performed a shutdown on the R2 PPP interface during negotiation.
• The Layer 3 protocol negotiation caused the connection failure.
15. Which two statements describe the function of time-division multiplexing? (Choose two.)
• Multiple data streams share one common channel.
• Conversations that require extra bandwidth receive any unused time slices.
• Time slots are utilized on a first-come, first-served basis.
• Time slots go unused if a sender has nothing to transmit.
• Priority can be dedicated to one data source.
16. When customers use credit cards to make purchases at a small business, a modem is heard dialing a telephone number to transfer the transaction data to the central office. What type of WAN serial connection is in use?
• leased line
• point-to-point
• circuit switched
• packet switched
17. Which best describes data communications equipment (DCE)?
• serves as data source and/or destination
• responsible for negotiating windowing and acknowledgements
• physical devices such as protocol translators and multiplexers
• equipment that forwards data and is responsible for the clocking signal
18. Permanent virtual circuits and switched virtual circuits are both part of which option for WAN connectivity?
• leased line
• cell switching
• packet switching
• circuit switching
19. Which field of a frame uses error detection mechanisms to verify that the frame is not damaged intransit?
• FCS
• MTU
• flag
• control
• protocol
20. What occurs in the encapsulation process as a data packet moves from a LAN across a WAN?
• The Layer 2 encapsulation changes to a format that is appropriate for the WAN technology.
• The Layer 3 encapsulation changes to a format that is appropriate for the WAN technology.
• Both Layer 2 and Layer 3 encapsulation change to a technology that is appropriate for the WAN.
• Both Layer 2 and Layer 3 encapsulation remain constant as the data packet travels throughout the network.
21. 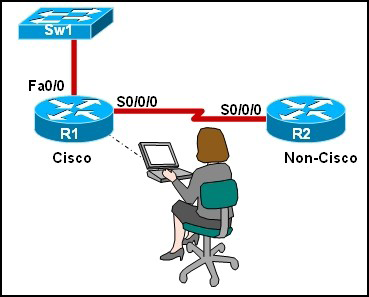
Refer to the exhibit. The network administrator is configuring R1 to connect to R2, which is a non-Cisco router. Which encapsulation method will need to be configured for communication to occur?
• HDLC
• HSSI
• ISDN
• IPCP
• PPP
22. A company is implementing dialup services for remote workers to connect to the local network. The company uses multiple Layer 3 protocols and requires authentication for security. Which protocol should be used for this remote access?
• LMI
• PPP
• HDLC
• Frame Relay
23. Which two options can LCP negotiate? (Choose two.)
• compression
• authentication
• dynamic flow control
• network layer address for IP
• connection-oriented or connectionless communication methods
24. What statement best describes cell switching?
• It uses a dedicated path between endpoints.
• It creates a permanent physical link between two points.
• It uses DLCIs to identify virtual circuits.
• It creates fixed-length packets that traverse virtual circuits.
But if you find the same answers for all the Module anywhere in the internet.
And if you have an Answers are correct 100% or if you find an answer, What is wrong in this blog. please send me. (Post in blog or Send Email )
Because,I will update the blog…
Tuesday, December 16, 2008
CCNA Discovery 3 - Module 7 Exam Answers Version 4.0
Subscribe to:
Post Comments
(
Atom
)
No comments :
Post a Comment